What is SSO?
SSO is an acronym that stands for single sign-on. Single sign-on allows user to one set of login credentials to access multiple applications. Much like a password manger which stores your login details and automatically logs you into a website, SSO can be used by companies to centralize the login, and user setup/provisioning to company tools.
What type of SSO does Blueprint support?
Blueprint can support SAML and OIDC
What is SP vs. IDP single sign-on?
SP stands for Service Provider and IDP stands for Identity Provider. These are terms used to describe how the SSO flow is initiated. An SSO event can be launched from the provider (i.e. Blueprint) side, or can be launched from the identity provider (i.e. you the client) side.
If you want to set up a dashboard with all of the applications your users can access, you will be using IDP initiated single sign-on. This is where your user is already logged into your system and clicks an icon of a tool or service and the authentication request is automatically sent to the provider to authenticate the user.
If you want your users to go to the Blueprint website and enter their email address to login, then you will be using the Service Provider initiated single sign-on.
Do you automatically provision new users?
Yes. When a valid SSO request is received, Blueprint will check to see if that user has logged in before. If they have not, the user will be automatically provisioned in our system.
Users do not need to be set up in Blueprint prior to using single sign-on.
If users already exist in Blueprint, they will be matched based on their email address and authenticated and authorized to that user in Blueprint.
Is SSO restricted to certain tiers or account levels?
No. Unlike others, we provide SSO for all our clients, regardless of their tier of service with us.
How do I setup SAML single sign-on?
To set up any single sign-on the user must have the correct roles and permissions. Refer to the Blueprint Role Manager for more details.
To set up SSO, go to ACCOUNT => CONFIGURE SSO
You will now see a Single Sign On Configuration page.
To set up SAML single sign-on, first select SAML from the dropdown list. Next, follow the instructions in the image below to populate the fields of the configuration.
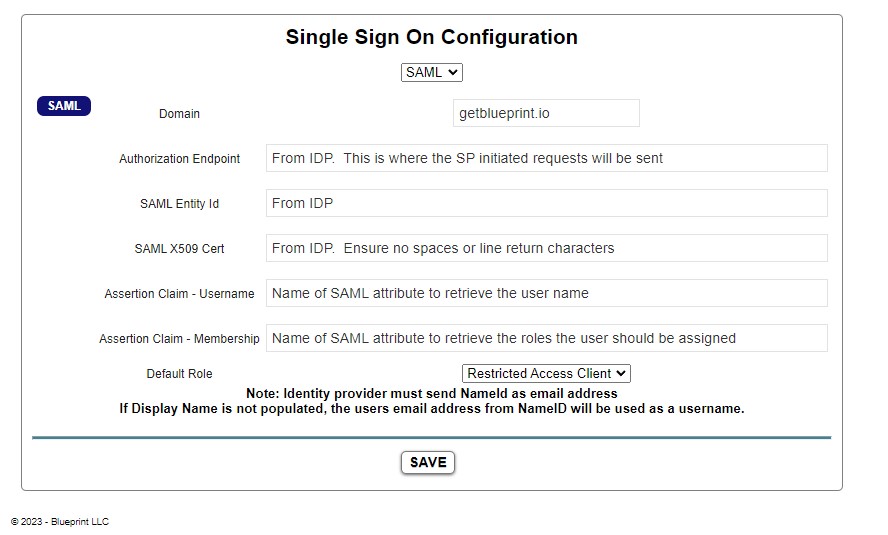
Set the Domain to your domain that will be sending the SAML response.
Blueprint is expecting the SAML response from the Identity Provider to contain a NameID field. If this field is not provided and error will occur.
The Username and Membership fields can be left out of the SAML response, but they are highly recommended. If a valid role is not provided in the Membership attribute of the SAML assertion, the user will be assigned the Default Role specified in the configuration. Administrators should be cautious to not set the Default Role to an overly permissive setting.
By default the user will be provisioned and their username will be their email. If you populate the Assertion Claim – Username you can provide an alternative name such as their employeeID or other descriptor to be used as the user name in Blueprint. Note, once the user is provisioned in Blueprint, further changes to the username field will not propagate and the username upon their provisioning in Blueprint will be used. If you have a pre-provisioned user and need to update their username, you will need to set up the Assertion Claim – Username, then delete the user from Blueprint manually. Upon their next SSO login the new username will be assigned.
The Identity Provider will need the following information to set up Blueprint
- SAML ACS URL: income.getblueprint.io/SSOSaml/Consume.aspx
- EntityID: Blueprint
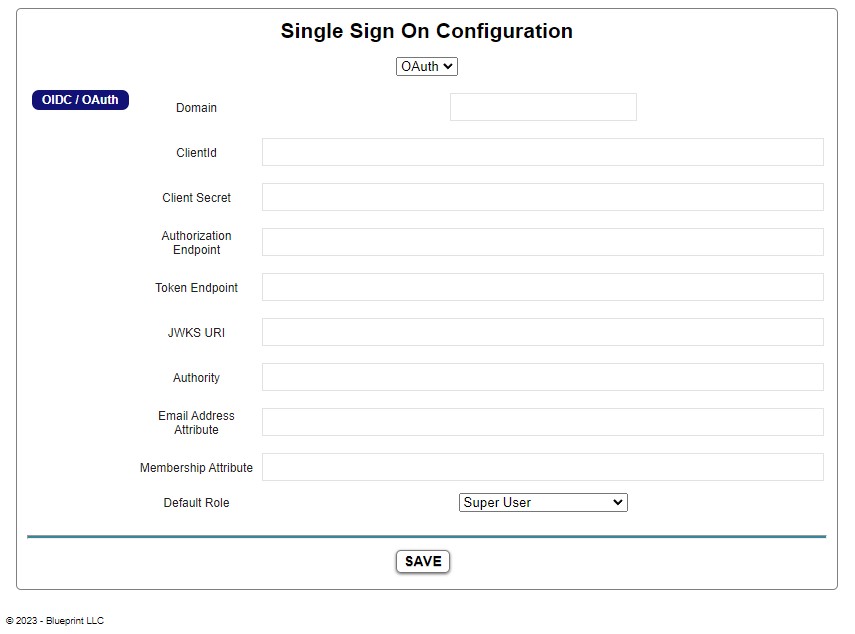
How do I setup OIDC single sign-on?
To set up any single sign-on the user must have the correct roles and permissions. Refer to the Blueprint Role Manager for more details.
To set up SSO, go to ACCOUNT => CONFIGURE SSO
Select OAuth from the dropdown list. Populate the configuration form with information from your Identity Provider.
How do I set assign roles to users with SSO?
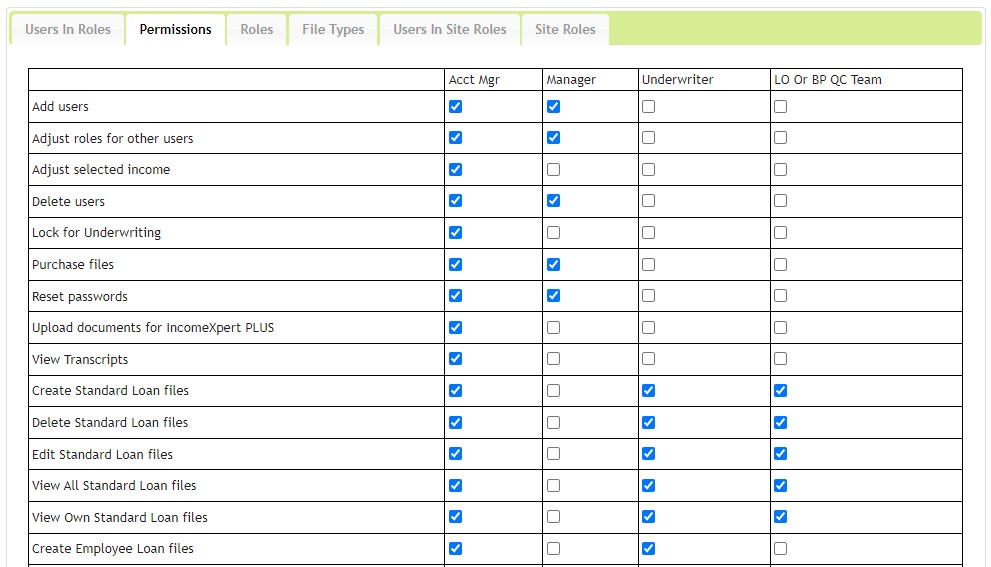
For SAML and OIDC the assertion claims response can accept role assignments. The role names passed in the SAML or OIDC response will be evaluated against the list of roles created in Blueprint. When a match is found, the user is assigned that role. When a role passed in the SAML or OIDC respond does not match, no role is assigned in Blueprint. If no valid roles are assigned, the default role selected in the SSO Configuration in Blueprint will be assigned.
In Blueprint the names of the Roles can be edited, or additional roles can be created. The permissions granted to a role are assigned in Blueprint and are not passed in the SAML or OIDC response. In short, remember the following key points
- Roles are defined in Blueprint
- Permissions are assigned to Roles in Blueprint
- Users are assigned to Roles in the SAML or OIDC response sent to Blueprint
- Roles are re-assigned on each session.
- Users will retain the permissions they are assigned until they logout or their session expires (4hrs)
- The role name in Blueprint must match the role name passed in the SAML or OIDC response in order for the user to be assigned that role
Can I have non-SSO users on the account?
Yes. Users with conventional username and password access can be on the account. It is recommended to limit this access to IT or Admin persons for security reasons.
Users with conventional username/password access should not access Blueprint using SSO. If a user with username/password access logs in with SSO their role assignment will be overridden with the role assignment from the SAML or OIDC response. This may result in a loss or elevation of access. Thus it is suggested to have users select one method of access and not mix methods.
